Privacy at Proxy
For most companies Privacy is a buzzword or a false promise — for us it’s everything. Proxy was created to ensure your right to control your privacy and personal data as technology enters the physical realm.
Privacy is a human right
We created Proxy to serve you. Full stop. Your data is your data. It’s owned by you and only you. Only you can consent to how it can be used and for what purposes, and if you change your mind you should be able to revoke access to your data from any party. These are not things we care about because of regulations. These are things we believe are fundamental to our humanity. No lengthy confusing privacy policy document should ever take that away.
Privacy principles
Here are the fundamental beliefs that drive our approach to data privacy.
01
We believe your privacy is a human right and is not something to be held at ransom.
02
We believe you own your personal data and digital self as much as your physical self, and you should hold absolute authority on how your data is shared and used.
03
We believe your personal data should be used to empower and positively serve you.
Privacy you can understand.
Nobody reads, let alone understands, privacy policies. They are designed by lawyers, for lawyers and are perfectly crafted to give companies the authority to take as much data and information from you as legally possible. That’s not right, and we’re putting our foot down.
Your data with Proxy, visualized
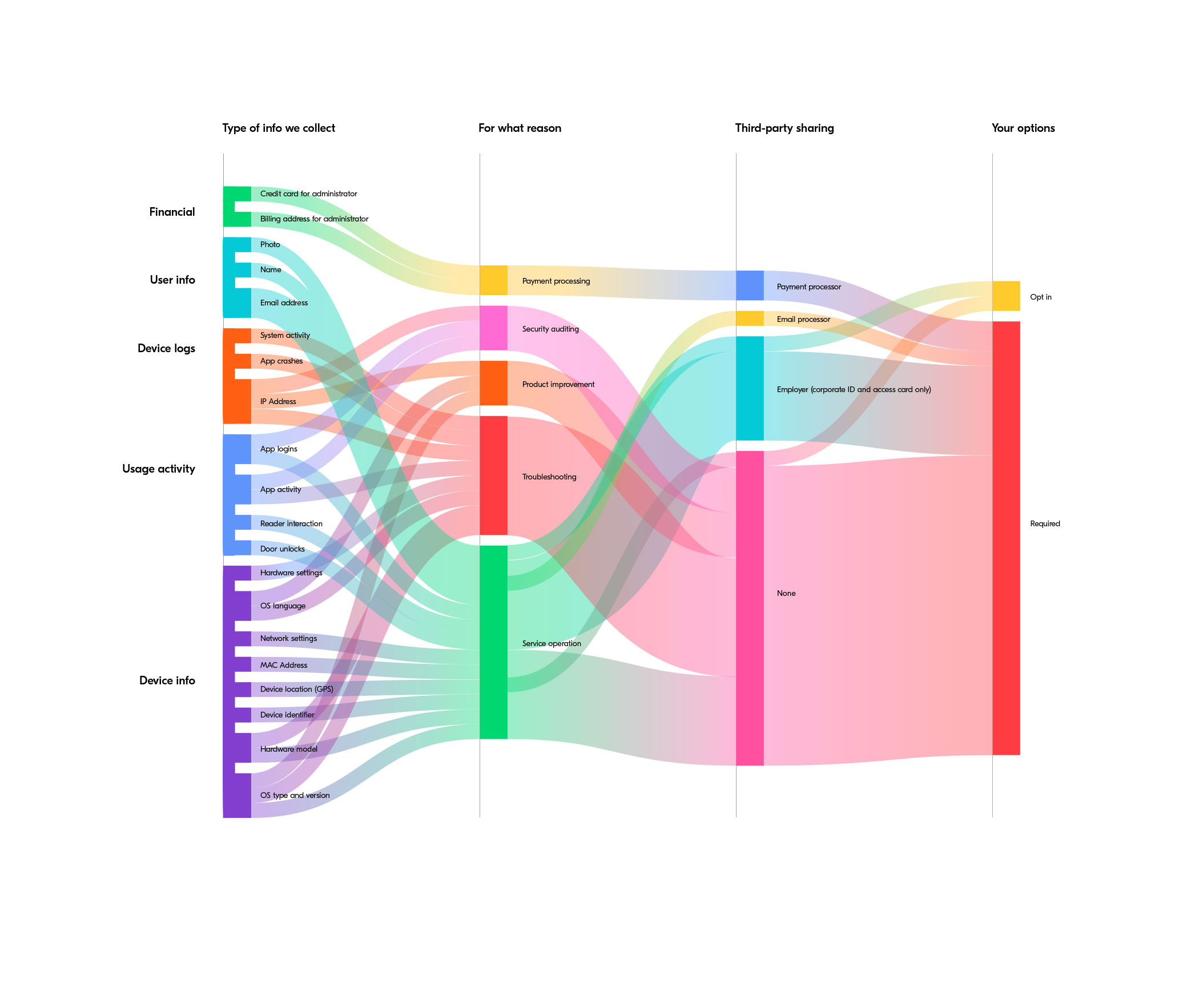
Proxy Privacy Policy
Proxy respects your privacy and is committed to protecting it. This privacy notice describes the types of information you may be asked to provide when using Proxy services, and our practices for using, storing, protecting, and disclosing that information.
Types of information
Profile information
You provide your name and photo when you activate Proxy on a new phone. You may optionally add other information to your profile, such as email addresses that link to your existing memberships and organization affiliations. Your name, photo, and email addresses are stored on our servers as part of your profile. You have the ability to delete this data by requesting deletion of your Proxy account.
ID information
Proxy provides services that allow you to digitize your physical ID cards and store them locally on your phone. To provide this service to you, Proxy uses third-party services that verify the validity of your ID card and match your face with the card photo. Your ID card information, card photo, and verification status are stored locally on your phone, and never stored on Proxy servers. The selfie taken during the ID verification process is stored on Proxy servers at a randomized URL known only to the local app on your phone. You have the ability to delete locally stored data at will by deactivating the Proxy app on your phone. Any link between your account and the selfie you previously verified is also removed at that time.
Health information
Proxy provides services that allow you to import your health test results and digitize your existing paper health documents. Your health test results and health documents are stored locally on your phone, and never stored on Proxy servers. If you have agreed to share your health status with another organisation, we will store only the overall status of the documents you provide, but never the documents themselves or any contained information, on Proxy servers. You have the ability to delete locally stored data at will by deactivating the Proxy app on your phone.
Proxy also allows you to complete a health survey. Survey answers you provide are never recorded or stored anywhere. If you have agreed to share your health status with another organisation, we will store only the overall pass or fail status of the survey, with the failure reason, on Proxy servers.
Usage information
App logins, interactions your phone has with Proxy devices, door unlocks, check-ins, and activity you perform within the Proxy app.
Phone information
Phone model, OS type, OS version, OS language, hardware settings, network settings, MAC address, device identifier and additional technical non-personal information as necessary for Proxy to operate our apps and services.
Diagnostic logs
Application logs including IP addresses, network requests made by the application, and crashes of the Proxy mobile app.
Financial information
Organisation administrators provide their company credit card number and billing address.
When and how your information is used
Information you provide
Profile information you provide is stored on Proxy servers. Your phone will transmit just your name and photo, for presentation purposes, to a check-in kiosk whenever you actively choose to check in at a supported location.
If you have agreed to share your verified ID status with another organisation, we will store only the verification status of your documents and the selfie you took during the verification process, but never the documents themselves or any contained information, on Proxy servers. We will provide this verification information to the requesting organisation.
If you have agreed to share your health status with another organisation, we will store only the overall pass or fail status of your health survey, the failure reason, and the status of your provided health documents, but never the documents themselves or any contained information, on Proxy servers. We will provide this status information to the requesting organisation.
Your phone will also anonymously transmit just the overall pass or fail status of your health survey, and the status of your documents but not the documents themselves, to a check-in kiosk when you choose to check in at supported locations.
If you are an administrator, business or paying user, the credit card and billing address information you provide is used for the purposes of processing payment.
Information organizations provide about you
Organizations that use the Proxy service may provide to us your name, email address, and photo when granting you access to buildings, check-in locations and issuing mobile ID cards. This data is owned by the organization and subject to the organisation’s privacy and data use policies, and is kept separate from your personal data.
Data provided automatically
All other information classified as Usage information, Phone information, and Diagnostic logs, is derived automatically when you use Proxy on your phone. Proxy limits this information, and the duration for which it is retained, to the minimum necessary to operate our services.
Why is this information relevant
Service operation
There are some core pieces of information that we need to make Proxy work. That includes the information in your user profile like your email address, and interactions whenever your phone running the Proxy app interacts with another Proxy device. In the background, the Proxy app also needs some data to operate properly on your phone such as your phone model and network settings. When interacting with other Proxy devices you have the option to share the status of your locally stored ID or health documents, name, photo, and date of birth.
Mobile app operation
The Proxy app accesses your phone’s GPS location services in order to “wake up” the Proxy app whenever you arrive at a place that you frequent (such as your office). We never store or transmit your GPS location. However, our logs of device interactions with Proxy devices could be used to infer your location if the location of the other Proxy device is known.
Contacting you about the Proxy services
We may use your email address to inform you about the service you signed up for, such as letting you know about upcoming changes to Proxy. We will also email you updates about service operation if you have opted to subscribe to updates from our status page at https://status.proxy.com.
We will not send you email about any services other than the one you signed up for without your explicit consent.
Troubleshooting
When you contact Proxy, we keep a record of your communication to help solve any issues you might be facing. Providing feedback in the Proxy app sends logs of your phone’s system activity and Proxy app crashes so that we can help troubleshoot. We also look at some other data to diagnose issues with the Proxy app including phone model, hardware settings, etc.
When interacting with our support staff, we will seek your consent before accessing any personal data or corporate data that you did not provide to us in your support request.
Security auditing
In order to prevent security incidents in the Proxy app and dashboard, and to investigate incidents after they have occurred, we retain IP addresses, activity in the Proxy app and dashboard, and login attempts.
Product improvement
We analyze and process some data to make Proxy products and services better, including IP addresses (which tells us in what geographic regions people are using Proxy), OS language, and OS type and version.
Payment processing
Proxy is free to install and use on your phone, but administrators that manage Proxy devices and associated software pay a subscription. We store payment details from those administrators for the sole purpose of processing payments.
Whom your information is shared with
We never sell or rent your personal information. In addition, we do not share or otherwise disclose such information except as described in this Privacy Policy.
Your employer or organizations you belong to
If you use Proxy as an employee or member of an organization, we share only the information relevant to your activities within that organization with its administrators. We never share any of your information that is not directly related to the organization in question (for example, your activity as part of other organizations which may also use Proxy services).
Payment processors
We share credit card and other payment details provided by administrators with our payment processors in order to facilitate payments to Proxy.
Email processors
In order to send you email related to Proxy, such as your verification email when you first sign up, we rely on email service providers to process and send these emails on our behalf. Our contracts with them prohibit sharing your email address and content with other third parties such as advertisers or marketing affiliates, or using it for any other purpose.
ID verification processors
In order to verify the validity of ID cards you digitize, we rely on service providers to process and verify scans of your ID documents. Our contracts with them prohibit sharing your information with other third parties such as advertisers or marketing affiliates, or using it for any other purpose.
Proxy uses the following providers to verify your ID documents:
Other third party processors
In addition to the processors above, we may disclose your information to other third parties to help us provide the Proxy services. Examples of such sharing include our web hosting services such as Amazon Web Services, our internal workflow tools like Dropbox and Salesforce, and our communications tools like Zendesk and Slack. When we disclose information to processors, we do so only after entering into a contract with the processor that describes the purpose of the sharing and requires the processor to both keep that information confidential and not use it for any purpose except performing the contract, helping to provide you the best Proxy service possible.
Law enforcement
We may also disclose your information if we are required to do so by a court order, law, or legal process, including to respond to government or regulatory requests. We will disclose no more than that portion of your information which we are legally obligated to disclose, and will use commercially reasonable efforts to obtain assurances from the applicable court or agency that your information will be treated with confidentiality.
Who owns what information
It is our intention to make you (the person) the owner of as much information related to your profile and transactions as possible, as opposed to only the companies with devices that sense your signal. Each transaction that occurs in the physical world is generated through interaction of several parties, each contributing their own data towards the outcome and deserving to retain their part of the result.
To better illustrate who owns what information, here are some examples of the most common Proxy transactions.
Person interacts with a Proxy device, after having accepted an invitation from an organisation
Let’s take the example of Jenna, who is using Proxy to check in and access the lobby and office of her employer Acme, Inc. Jenna has an access pass for Acme, Inc. in her Proxy mobile app. Acme, Inc.’s access control system is connected to that of its landlord, Buildings, Inc. Who owns what data?
1. Jenna is invited to use Proxy by her employer, Acme
- Jenna: —
- Acme: Jenna’s work email address, name from the corporate HR system (optional), photo from the corporate HR system (optional), and keycard number
- Landlord: —
- Proxy: Metadata of the transaction (may include IP address, timestamp, device operating system, Proxy app version)
2. Jenna creates a Proxy account and links her work email address
- Jenna: Jenna’s name of choice (e.g. Jen), photo from her gallery (optional)
- Acme: —
- Landlord: —
- Proxy: Metadata of the transaction (may include IP address, timestamp, device operating system, Proxy app version)
3. Jenna accepts the invitation to add an Acme access pass to her Proxy app
- Jenna: "Jenna accepted a pass from Acme, Inc."
- Acme: "Jenna accepted a card from Acme, Inc."
- Landlord: —
- Proxy: Auditable record of Jenna’s consent, and metadata of the transaction
4. Jenna walks through a turnstile in the lobby of the building
- Jenna: "Jenna activated a turnstile and was granted access by Acme, Inc."
- Acme: "Jenna with this keycard number activated a turnstile."
- Landlord: "Employee of Acme, Inc. activated Turnstile A at 555 7th Ave."
- Proxy: "User ID number interacted with sensor ID number."
5. Jenna unlocks an office door on her floor
- Jenna: "Jenna unlocked a door and was granted access by Acme, Inc."
- Acme: "Jenna unlocked Office Door 103."
- Landlord: —
- Proxy: "User ID number interacted with sensor ID number."
6. Jenna checks in at the reception of Acme when entering the office by bumping her phone at a Proxy check-in kiosk owned by Acme
- Jenna: "Jenna has shared her name, photo and health status with Acme"
- Acme: "Acme locally verifies the information that was shared, and optionally stores a record of the event that Jenna checked in successfully, as well as the verification status of Jenna’s ID and health documents. Acme never receives copies of these documents."
- Landlord: —
- Proxy: "Auditable record of Jenna’s check-in, and metadata of the transaction."
While the parties remain in a relationship (Jenna is still employed by Acme, Acme is still a tenant in the building), they have visibility of the full data associated with the transaction — Jenna and Acme both have a record of which office doors she unlocked, or which locations she checked in at, and Acme is able to detect Jenna’s Proxy signal while she is inside the building.
Once their relationship is terminated, each party keeps just their perspective of the transaction — Jenna still has a record that she unlocked a door and/or checked in at Acme, Inc., but no longer has access to identifying information about Acme’s office locations. Respectively, Acme loses access to any updated information about Jenna other than what Acme provided themselves, and is no longer able to detect her Proxy signal inside the building.
Person passively detected by a Proxy device (invited, but not accepted)
Keeping with our example, let’s look at a situation where a company called Irrelevant Co. invites Jenna to use a mobile access pass for a meeting, and she rejects the pass invitation. When she arrives for her meeting, she walks by a Proxy device owned by Irrelevant Co.
1. Jenna ignores or rejects the invitation from Irrelevant Co.
- Jenna: "Jenna rejected a pass from Irrelevant Co."
- Acme: —
- Irrelevant Co: "Jenna rejected a pass from Irrelevant Co."
- Proxy: Auditable record of Jenna’s rejection, and metadata of the transaction
2. Jenna walks past a Proxy reader owned by Irrelevant Co.
- Jenna: —
- Acme: —
- Other Co: —
- Proxy: "Access is denied for user ID number detected by sensor ID number."
3. Jenna walks past a Proxy check-in kiosk owned by Irrelevant Co.
- Jenna: —
- Acme: —
- Other Co: —
- Proxy: —
Person detected by a Proxy device in proximity (never invited)
Let’s look at a scenario where Jenna walks past a Proxy device owned by a company she has no existing relationship with, Other Co. In this scenario we also consider an example where Jenna actively chooses to check in at a Proxy device owned by Other Co. by bumping her phone.
1. Jenna walks past a Proxy reader owned by Other Co.
- Jenna: —
- Acme: —
- Other Co: —
- Proxy: "User ID number detected by sensor ID number."
2. Jenna walks past a Proxy check-in kiosk owned by Other Co.
- Jenna: "There is a Proxy check-in kiosk nearby"
- Acme: —
- Other Co: —
- Proxy: —
3. Jenna bumps her phone at a Proxy check-in kiosk owned by Other Co to check in
- Jenna: Jenna accepts to share her name, photo and health status with the kiosk, and sees the name of the kiosk.
- Acme: —
- Other Co: "An anonymous person met the check-in acceptance criteria by providing valid information to the kiosk."
- Proxy: Metadata of the transaction, not tied to Jenna (may include IP address, timestamp, device operating system, Proxy app version)
Person bumps their phone with another Proxy user in proximity
Finally, let’s look at an example where Jenna wants to share certain personal information with her peer Joe, another Proxy user.
1. Jenna bumps her phone with Joe to share her date of birth, name and photo
- Jenna: Jenna bumps her phone with Joe, who is asking for her verified date of birth, name and photo. Jenna sees an ephemeral view of Joe’s request, including his profile name and photo: "Joe requested your date of birth, name and photo."
- Joe: Joe sees an ephemeral view of Jenna’s profile name and photo
- Acme: —
- Proxy: Metadata of the transaction, not tied to Jenna or Joe (may include IP address, timestamp, device operating system, Proxy app version)
2. Jenna accepts the information request from Joe
- Jenna: "Jenna has shared her verified date of birth, name and photo with Joe."
- Joe: "Jenna has shared her verified date of birth, name and photo with Joe.” Jenna’s actual information displayed on Joe’s phone vanishes after 30 seconds."
- Acme: —
- Proxy: Metadata of the transaction, not tied to Jenna or Joe (may include IP address, timestamp, device operating system, Proxy app version)
Your privacy options and rights
Your options
You can elect to not provide some information
You don’t have to upload a photo to your Proxy profile and you can decide not to enable location services to the Proxy app on your phone.
While location services are optional, enabling it is only needed for the purposes of improving the user experience by not having to launch the app every time you interact with a device or check-in. Location information is never stored or shared, and only used to wake-up the app when you are in proximity to a Proxy device.
Your rights
You have the right to see the information we store about you
You have the right to ask for information we have about you, and how we use that information. Once we receive and verify your request, within 45 days we will disclose to you:
- The categories of personal information we have about you
- The sources of that information
- Our purpose for that information
- The categories of third parties with whom we share that information
- The specific pieces of your personal information
You have the right to correct any inaccuracies in your personal information
You can update information in your Proxy profile, such as your name and photo, from within the Proxy app. To update other information about you, you can contact privacy@proxy.com. We will honor your request to update your information unless we are required to keep the existing information for legitimate contractual or legal purposes.
If you believe that your employer or another organisation has inaccurate information about you, you can contact that organization to update your information as the data controller. We will honor the controller’s request to update any information they control.
You have the right to have information about you deleted
You may request that we delete any information that we have received from you and retained, subject to certain exceptions. These exceptions include completing the transaction or providing the service you requested, complying with legal obligations, or detecting and preventing security incidents or illegal or fraudulent activity.
How we secure data
We use physical, technological, and administrative measures to secure your data. For more information, visit our security page.
Where we store data
We store data in data centers in the United States and Ireland. Additionally, your information that is shared with third parties is stored in any location they have data centers. Data transmitted between Proxy and third parties, or between our servers and applications, may be cached temporarily during transit or locally on receiving devices only for the purpose of improving performance and reliability of the service.
Updates to this policy
When we make minor edits to this policy, we will make the changes on this webpage and describe the edits at the top of the page. For more extensive updates, we will send an email with details to the email address you have provided.